To frame the problem let us take an inductive look at the question of why do we care about data destruction well it is one of many security controls that the cloud security alliance teaches us to review before engaging with a cloud service provider csp.
Aws secure data destruction.
Customer content and account information.
Here is a quote from an amazon document about their data security.
Overview of security processes page 2 features such as individual user accounts and credentials ssl tls for data transmissions and user activity logging that you should configure no matter which aws service you use.
Uses machine learning to automatically.
Each aws account has a unique master key that is stored separately from your data on a system that is surrounded with strong physical and logical security controls.
Degaussing uses a high powered magnetic field that permanently destroys data on the platters.
Each encrypted volume and its subsequent snapshots is encrypted with a unique volume encryption key that is then encrypted with a region specific secure master key.
Storage media which is being decommissioned will be passed to a specialist contractor for secure disposal.
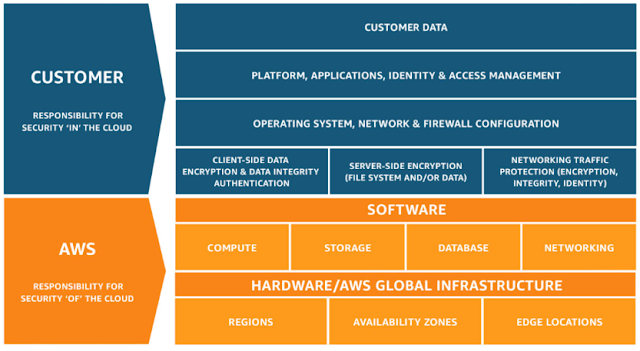
Security of the cloud aws is responsible for protecting the infrastructure that runs aws services in the aws cloud.
Amazon web services amazon web services.
Aws classifies customer data into two categories.
A hard disk destruction.
When an object is deleted from amazon s3 removal of the mapping from the public name to the object starts immediately and is generally processed across the.
Degaussing is a simple method that permanently destroys all data and disables the drive.
When i teach about cloud security i remind my audience that a given security control only mitigates specific risks and that in.
The effectiveness of our security is regularly tested and verified by third party auditors as part of the aws compliance programs.
Then amazon designates that area of disk for write only operations so that your data gets overwritten quickly.
Before we build a data center we spend countless hours considering potential threats and designing implementing and testing controls to ensure the systems technology and people we deploy counteract risk.
Accommodate the multiple levels of access and nuances for implementing a secure but still usable approach for each level.
For more information about these security features see the aws.
We define customer content as software including machine images data text audio video or images that a customer or any end user transfers to us for processing storage or hosting by aws services in connection with that customer s account and any computational results that a customer or any end.